Cybersecurity
Cybersecurity
Protect your business in the digital age with Awsome LLC’s cybersecurity solutions. Our tailored offerings include vulnerability assessments, firewall protection, intrusion detection, data encryption, multi-factor authentication, and incident response. With expertise, continuous monitoring, compliance assurance, and peace of mind, we ensure your business remains resilient against cyber threats. Partner with us for a secure digital future. Contact us today.
Why Device Categorization Matters ?
Device categorization is fundamental for medical device manufacturers, determining the regulatory pathway for market approval and guiding healthcare professionals and consumers in their decisions. Understanding each device’s classification is essential in tailoring our penetration testing services to meet specific regulatory requirements and address potential risks effectively.
Our Penetration Testing Approach
Penetration testing is a critical component of a robust cybersecurity strategy for medical devices. It identifies vulnerabilities and ensures compliance with the highest security standards. Our comprehensive penetration testing services include:
- Network Penetration Testing: Identifies vulnerabilities in your network infrastructure to protect against unauthorized access.
- Web Application Penetration Testing: Assesses the security of your web applications to prevent data breaches and attacks.
- Wireless Penetration Testing: Evaluates the security of wireless networks, safeguarding against unauthorized access and ensuring data integrity.
- Physical Penetration Testing: Tests the physical security measures of your facilities to prevent unauthorized access to sensitive locations.
- Social Engineering Penetration Testing: Measures employee resilience against social engineering and phishing attacks.
- Client-Side Penetration Testing: Enhances the security of applications and environments on the user’s device.
Compliance and Standards
We ensure compliance with leading standards and frameworks, including NIST, CIS, OWASP, OSSTMM, ISSAF, and PTES, offering:
- Concept Evaluation: Assess compliance with international standards, cybersecurity practices, and regulatory requirements.
- Vulnerability Scans: Identify and remediate known weaknesses in systems and applications.
- Penetration and Fuzz Testing: Simulate cyber attacks to uncover unknown vulnerabilities, enhancing the security of medical devices or software.
Penetration Testing Process
Our penetration testing process is designed to thoroughly assess and enhance the cybersecurity of your medical devices:
- Model: Develop comprehensive Threat, Incident Response, and Organization Models.
- Attack: Conduct reconnaissance and exploit vulnerabilities to assess security measures.
- Repair: Provide targeted recommendations to address vulnerabilities and document findings.
- Assess: Evaluate the impact of attacks and assess overall security posture, ensuring a resilient defense against cyber threats.
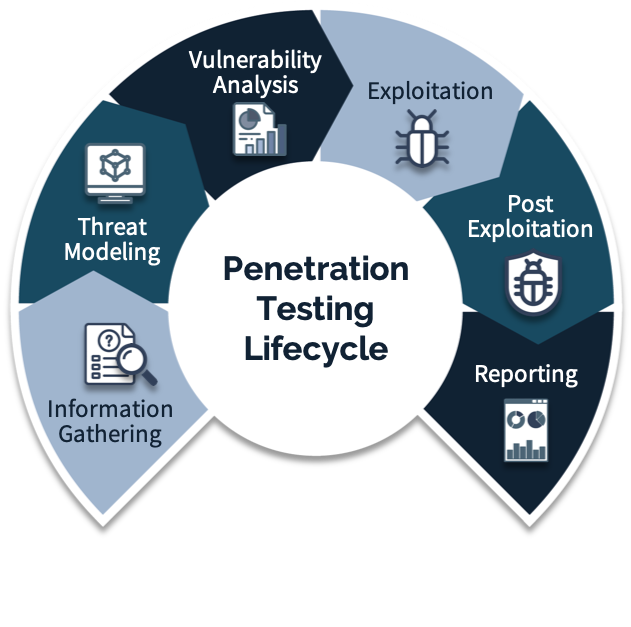
Penetration Testing Process
Our penetration testing process is designed to thoroughly assess and enhance the cybersecurity of your medical devices:
- Model: Develop comprehensive Threat, Incident Response, and Organization Models.
- Attack: Conduct reconnaissance and exploit vulnerabilities to assess security measures.
- Repair: Provide targeted recommendations to address vulnerabilities and document findings.
- Assess: Evaluate the impact of attacks and assess overall security posture, ensuring a resilient defense against cyber threats.
Elevating Cybersecurity in Medical Devices
Our approach aligns with major regulatory authorities, incorporating a strong quality management system to enhance customer satisfaction, foster loyalty, and promote recurring business. Entrust us to fortify your medical devices against evolving cybersecurity threats, ensuring compliance, and safeguarding patient data.
Contact us to learn more about our penetration testing services and how we can help secure your medical devices.


